
Discover the real-world impact of BEC attacks and how Huntress Managed ITDR can shield businesses with expert threat detection and response.
Stop the hacker who stole your CEO's email
Just one compromised account is all it takes for attackers to pose as your company’s leadership, reroute payments, and quietly drain your funds. Huntress stops takeovers before the fallout and trains users to spot Business Email Compromise (BEC) so you stay protected.
Yes, if you have the right visibility across your network and systems. These days, many initial access broker groups and ransomware gangs rely on weaknesses in security tools like firewalls and VPNs to gain access to a network. But they can’t do it quietly, making it possible to detect attacks through log and event monitoring.
Ransomware groups prey on employees because they can provide an expressway into a network. Employees can be phished to install an attackers' tools or steal administrative passwords making it easy to compromise a network.


Ransomware groups prey on employees because they can provide an expressway into a network. Employees can be phished to install an attackers' tools or steal administrative passwords making it easy to compromise a network.
The sinking feeling of a user reporting a clicked phishing link quickly confirms a compromised account via an unusual datacenter IP login. This triggers a frantic scramble to assess the damage, determine responders, and contain the threat.
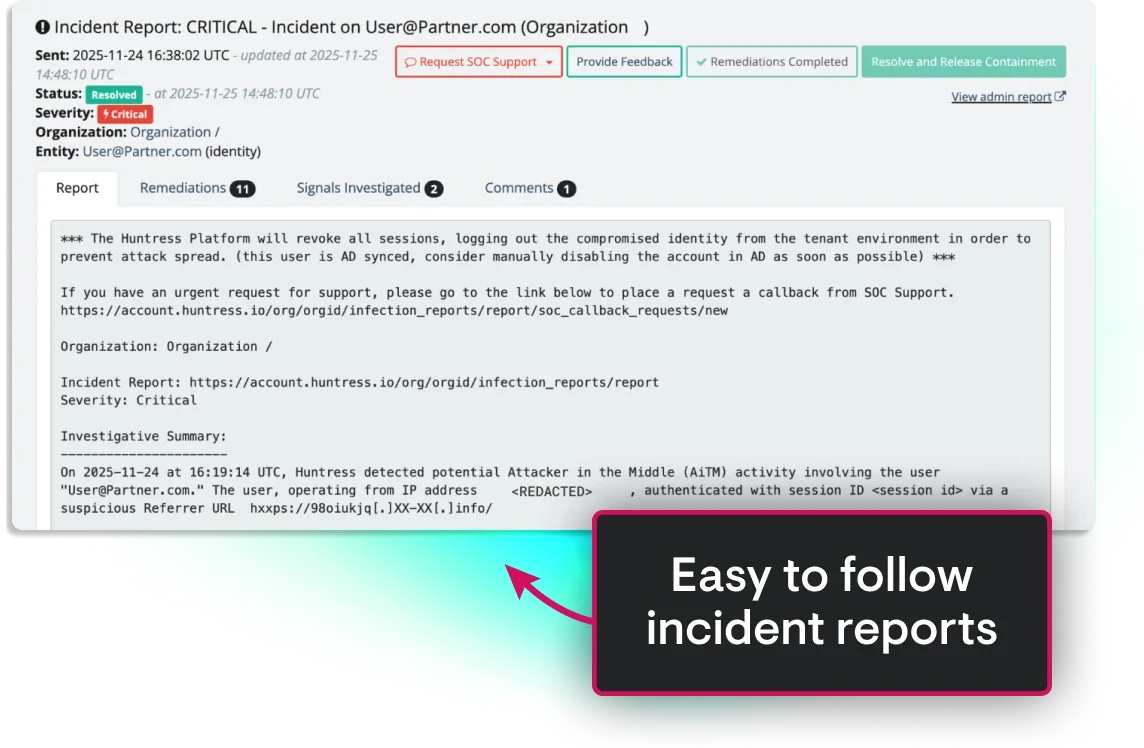
With the 24/7 Huntress SOC, that panic is eliminated. We contain threats within minutes, completing critical, time-sensitive steps before attackers can steal data or initiate wire fraud by:

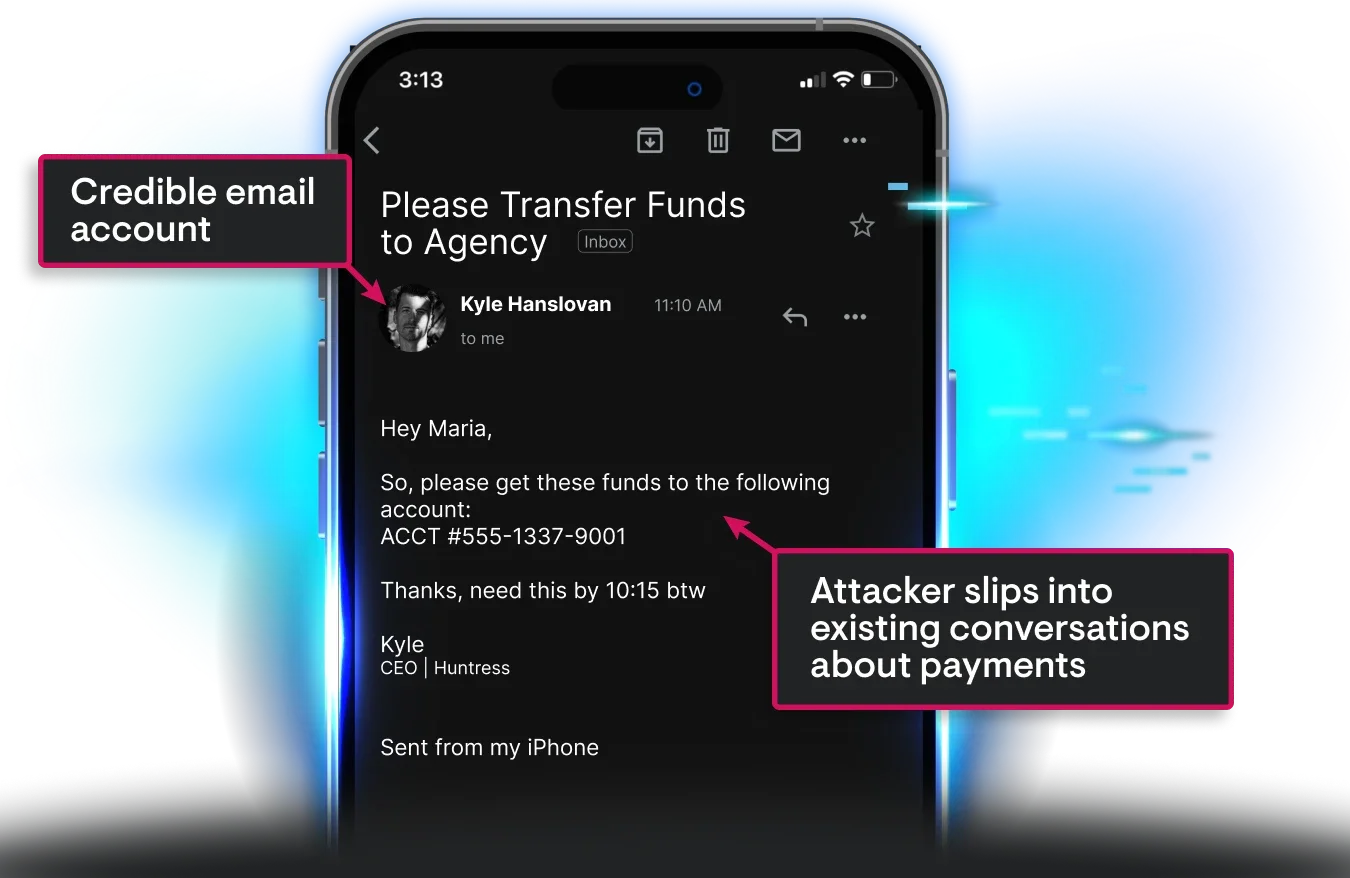
The real danger of BEC isn’t the message you never saw. It’s what happens once attackers are lurking around your inbox.
With Huntress, you’re never alone in the fight against BEC. Our SOC staffed by elite threat analysts is ready to shut down attacks 24/7 to keep your business secure, your operations steady, and your peace of mind intact.

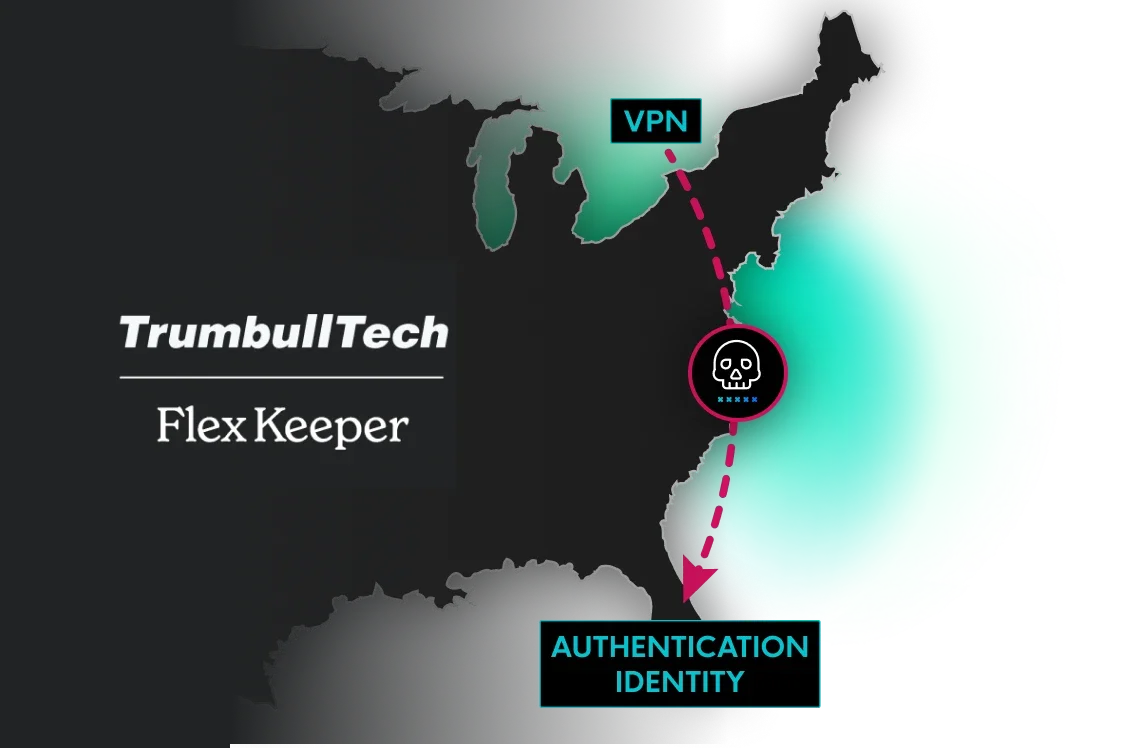
One phishing email almost cost an accounting firm everything. But Huntress caught the intruder inside Microsoft 365 and shut down the attack in minutes. This case study reveals just how fast BEC can happen and why it often catches businesses by surprise.
If you worry about a user clicking a bad link or an account being quietly hijacked, this story will hit close to home.
Learn how FlexKeeper dodged a financial disaster, and what it means for your own security.See how Huntress swapped their growing pains for effortless, scalable protection, helping them onboard seven tenants in just two weeks and putting control firmly back in their hands.


Global threat analyst coverage
Led by a team of elite, industry-recognized threat analysts who’ve seen it all, our 24/7, AI-assisted SOC works around the clock to find and eliminate ransomware threats before they can damage your business.
Mean Time to Respond (MTTR)
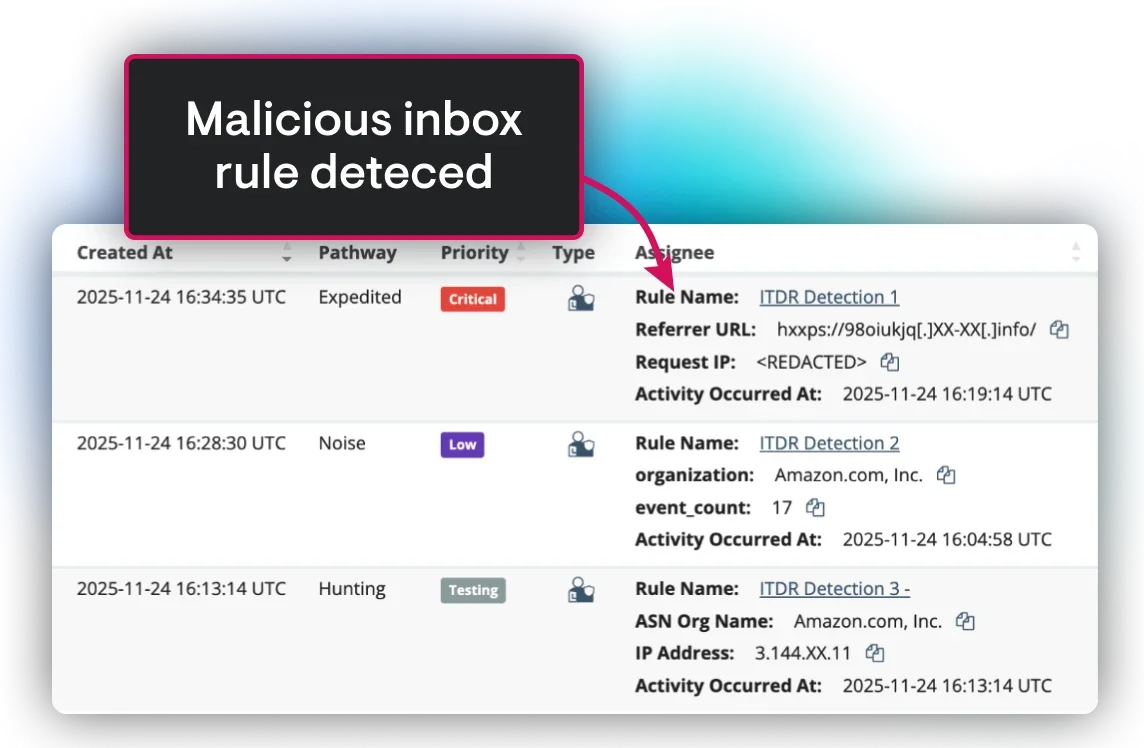
Once attackers compromise an identity, they forward rules, hijack sessions, and set up fraudulent payments. They move fast, but Managed ITDR moves faster. Our 3-minute MTTR stops attackers before a compromised inbox turns into a full-blown BEC incident.
Organizations protected by Huntress
We see millions of attacks each year, and every one of them makes us smarter. These insights constantly evolve our tech and our approach to wrecking hackers. The result is greater efficiency for your team and herd immunity across our customers.
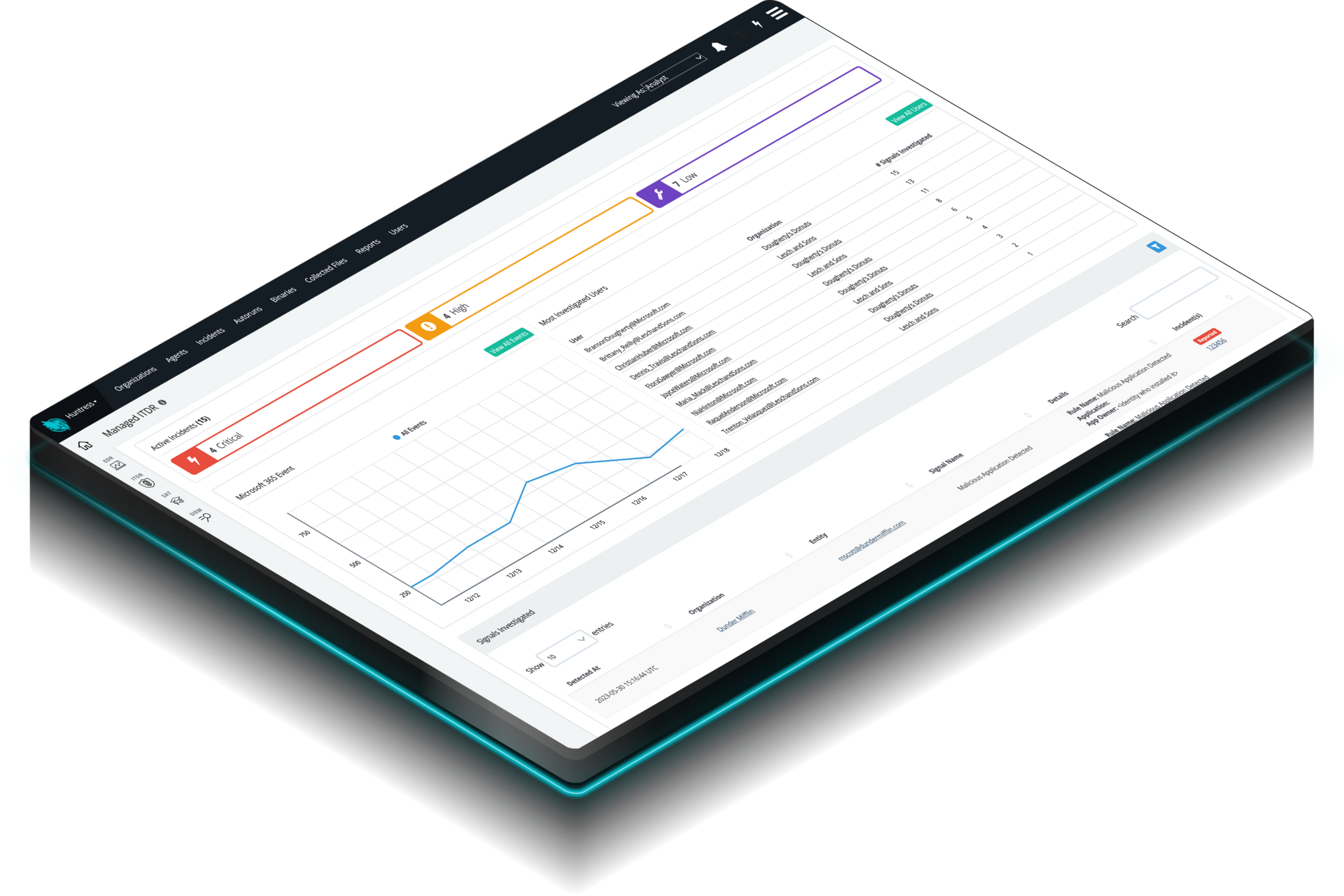






Identity Threat Detection and Response (ITDR)
Finds and stops identity-based threats in Microsoft 365—because identity is the new endpoint, and attackers know it. Huntress Managed ITDR is designed to detect, respond to, and resolve critical identity-based threats like account takeovers, business email compromise, unauthorized logins, and more.
Engaging, expert-backed, personalized training content built on real-world threat intelligence and created by Emmy® Award-winning animators to reduce human risk and build a strong security culture.
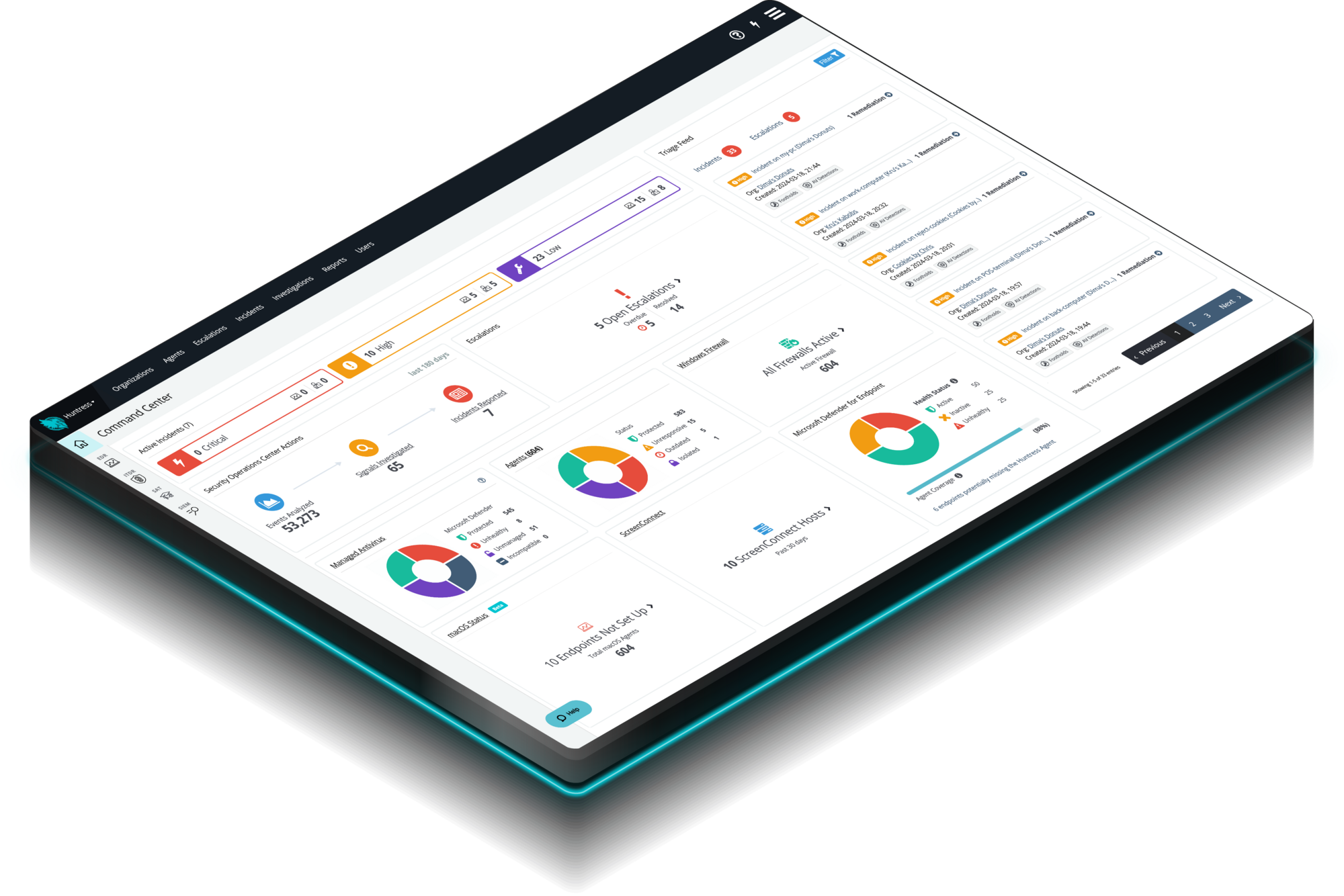
Huntress Managed EDR doesn't just watch your endpoints—it’s a complete solution. From the second a threat appears until it’s eliminated, we handle everything. You get 24/7 continuous protection, detection, and response that disrupts and remediates threats.
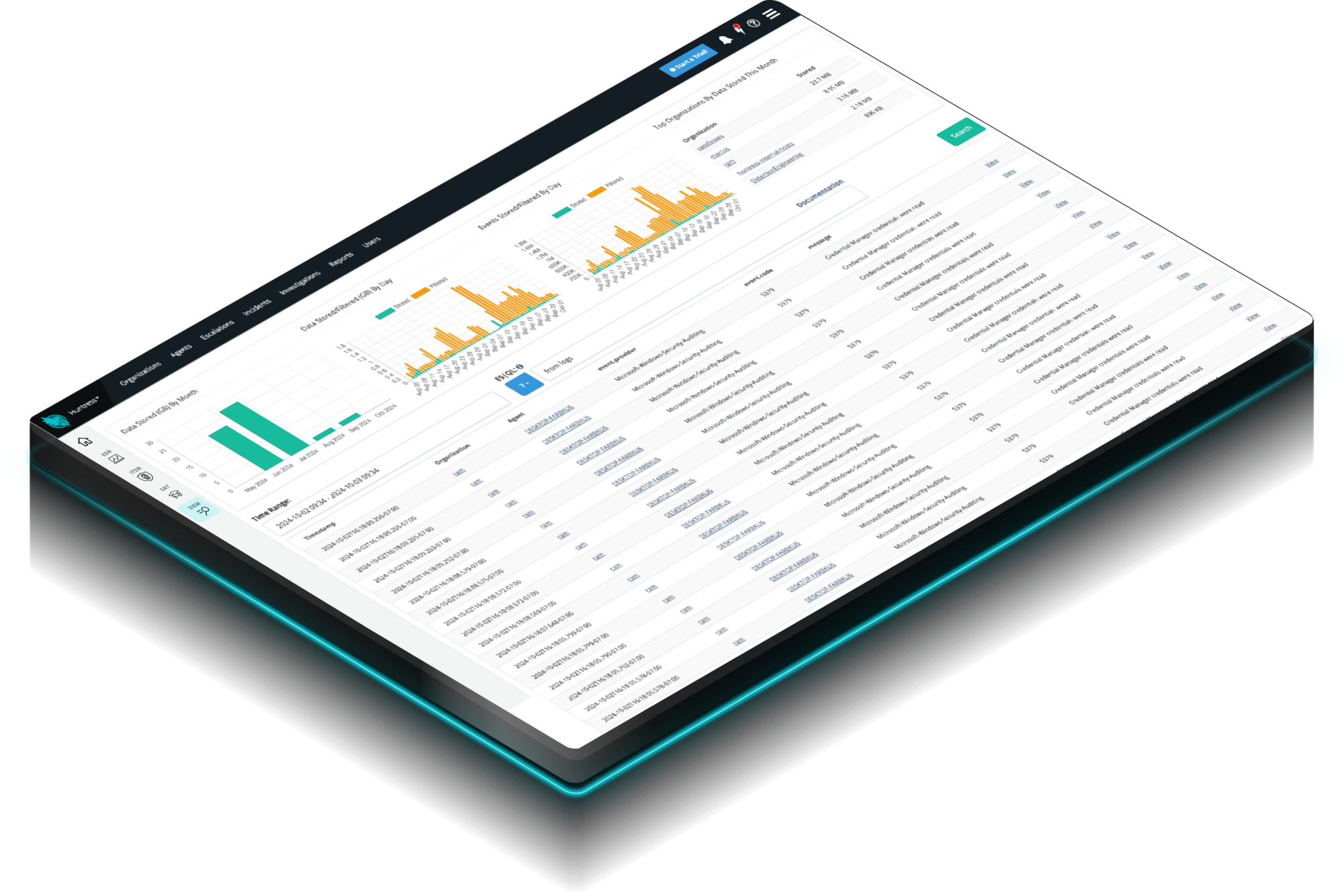
Huntress Managed SIEM takes away the complexity and overhead usually associated with traditional SIEMs, giving you everything you need and nothing you don’t. 24/7 threat response and strengthened compliance, fully managed by SOC experts, at a predictable price.


Overall Winner: Security – Identity

Fortune Cyber 60
Security Awareness Training Platform of the Year






Traditional tools focus on the email itself. We focus on the identity after a successful login. Our Identity Threat Detection and Response (ITDR) solution continuously monitors your M365 accounts for post-compromise activity, such as suspicious mail rules, rogue application access, and lateral movement. This unique focus, backed by our human-led, AI-assisted SOC, ensures we detect and stop attackers who bypass perimeter controls. We provide true 24/7 coverage, turning noise into verified, actionable threats that directly prevent wire fraud and data loss.
Huntress is designed specifically for teams like yours. Our human-led, AI-assisted SOC acts as your dedicated extension, providing the necessary expertise and 24/7 coverage without the massive cost or complexity of building or scaling your own security team. We handle the hard parts—threat hunting, investigation, and response—and deliver concise, verified actions to your team. This model ensures you get enterprise-grade security outcomes without needing enterprise resources.
Speed is critical in BEC defense. Our SOC is investigates and responds to verified account takeovers in Microsoft 365 with an average mean-time-to-respond (MTTR) of under 3 minutes. This rapid, human-led intervention minimizes the attacker's window of opportunity to pivot to financial fraud or change critical settings. We don't just alert you; we start the containment process immediately to protect your business assets.
Yes, when done correctly. Our Security Awareness Training goes beyond generic training to effectively manage and reduce human risk. We equip your team to identify threats with content built on real-world BEC tradecraft observed by our own SOC and security experts. The training is highly engaging and built to reduce incidents caused by human risk. By combining advanced identity protection (ITDR) with targeted, up-to-date human training, we ensure that both your technology and your people are prepared to defend against the latest threats.
Huntress Managed ITDR is fundamentally different from email security solutions because it defends against identity-based attacks, not just email-borne ones.
Here’s how they differ:
1. Broader scope beyond email.
Email security tools focus on filtering spam, phishing, and malicious attachments. Huntress Managed ITDR continuously monitors the entire Microsoft 365 identity ecosystem—logins, OAuth applications, session tokens, and configuration changes—to catch threats that bypass the inbox entirely.
2. Detects threats after compromise.
Even if an attacker phishes a user and gains access, email tools often stop there. Managed ITDR detects and responds to the post-access activity—suspicious logins, rogue OAuth apps, unusual inbox rules, and lateral movement attempts—that indicate an active identity attack in progress.
3. Protects the cloud, not just communications.
Modern attacks don’t always arrive via email—they exploit trusted apps, credentials, and tokens. Managed ITDR closes that blind spot by detecting unwanted access across Microsoft 365 and Azure AD, including non-email vectors like SharePoint and Entra ID.
4. 100% managed detection and response.
Unlike standalone email gateways or filters, Managed ITDR combines automated detections with 24/7 human SOC investigation and response—disabling compromised accounts, removing rogue apps, and containing threats in real time.

Discover the real-world impact of BEC attacks and how Huntress Managed ITDR can shield businesses with expert threat detection and response.

Our platform combines a suite of powerful managed detection and response tools for endpoints and Microsoft 365 identities, science-backed security awareness training, Managed SIEM, and the expertise of our 24/7 Security Operations Center (SOC).